
Microsoft have released the preview of “Microsoft Sentinel for Power Platform” without much fanfare (overshadowed by Copilot really) but I think it could be a very interesting offering. Microsoft Sentinel is a SIEM (security information event and management) platform, aimed at enabling organisations to monitor, discover, remediate, and prevent security attacks across their organisation.
Low code risks
As more and more users develop low code applications within organisations, the risks to those businesses increase. The apps will connect to various internal and external systems, containing and moving data – some of which may be sensitive and/or covered by regulations such as the GDPR or HIPAA – and perhaps linking to web servers and SaaS applications too.
Applications created by highly trained developers with years of experience and huge budgets often suffer from security weaknesses; one can only imagine the potential problems with apps created by citizen developers!
Microsoft Sentinel for Power Platform
This will enable organisations to monitor Power Platform environments and detect any suspicious activity such as:
- Power Apps execution from unauthorized geographies
- Suspicious data destruction by Power Apps
- Mass deletion of Power Apps
- Phishing attacks made possible through Power Apps
- Power Automate flows activity by departing employees
- Microsoft Power Platform connectors added to the an environment
- Update or removal of Microsoft Power Platform data loss prevention (DLP) policies
The initial rules included are:
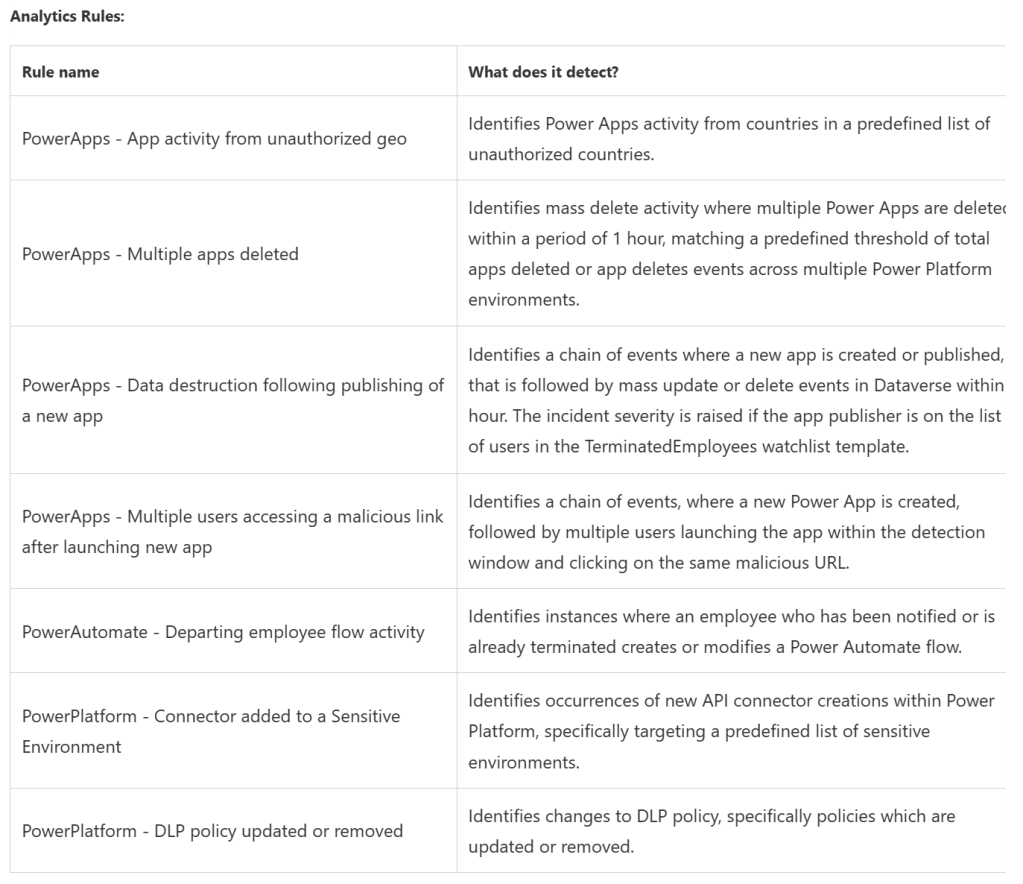
but as we’ve seen with Microsoft Sentinel itself, these will be added to over time.
Almost every organisation will find itself with a large Power App and Power Automate user base so Sentinel for Power Platform could really be worthwhile.
