Microsoft Windows InTune is the new Cloud based systems management tool from Microsoft, formerly known as “System Center Online” and has been long awaited. The ability to manage multiple locations/organizations from one central, online point is attractive to a lot of people for a lot of reasons…so let’s take a look @ InTune.
There are at least 10 sections inside InTune so I’m going to cover them in a number of posts, we’ll start with – System Overview:


This is the first screen you see when you log in to the Windows InTune Admin Console and it immediately gives you a great overview of yours systems. It shows:
- If Machines are infected/unprotected
- If there are updates for your machines
- A number of other alerts
Malware Protection:
From here you can see which machines have Malware protection turned off completely and also if they have overdue scans or specific parts of the protection, such as USB device scanning, turned off.
1 click takes you to a list of machines, from where you can turn on protection.
Updates:
This, not surprisingly, gives you a list of all the updates that are available for you machines be they for the OS or applications.
One issue with this is that, as default, it shows you ALL possible updates:

however, these can easily be filtered:


Another problem I have noticed is that it wants to give my laptop updates for Office 2007, as well as Office 2010; oddly, this doesn’t happen with my other 2010 machines. I had a number of issues when upgrading Office versions and I’m inclined to believe that there are some Office 2007 remnants on the machine that are being picked up by Intune.
Should you choose to approve an update for a machine/machines, you then reach this screen:
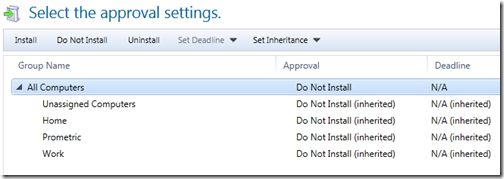
Choose the groups on which you want to install the updates, click approve and job done!
I feel it would be a smoother experience and require less clicks, if you could see the machine names on the same screen as all the updates. Currently, you must:
- Select the update
- click on “x computers need this update”
- Check the groups/machines
- Go back to the previous screen
- Approve Update
Showing the machines names/groups on the initial screen would remove a lot of that.
You can also access the updates via the individual machine screen, I’ll cover that in a later post.
Alerts by Type:
This section, as well as the above, also includes other types of alerts…not just updates and malware. This is where InTune starts to differentiate itself from other products, for example:

If I click through, it tell me:

That is pretty cool, and something that is very useful for System Admins. I didn’t expect InTune to cover things like this, certainly not in the beta, so I’m pleasantly surprised  However, you can’t initiate the defrag from InTune.
However, you can’t initiate the defrag from InTune.
The 2 options on the right hand side “Create Computer Group” and “View a Report” will be covered in later posts.
Summary:
This is a brief look at just the first screen of Microsoft Windows InTune but I’m sure you will agree that it already looks very interesting. So stay tuned for the remaining posts in this series (at least 9!) and ask any questions you may have in the comments 
Cheers
Rich